NetworkMiner adalah software
Analisis Jaringan Forensik untuk Windows. NetworkMiner ini bisa digunakan
sebagai alat sniffer / paket jaringan pasif menangkap data, seperti missal
gambar.
Download : http://www.netresec.com/?page=NetworkMiner
Cara penggunaannya, setelah
menjalankan NetworkMiner maka pilih network adapter yang digunakan.
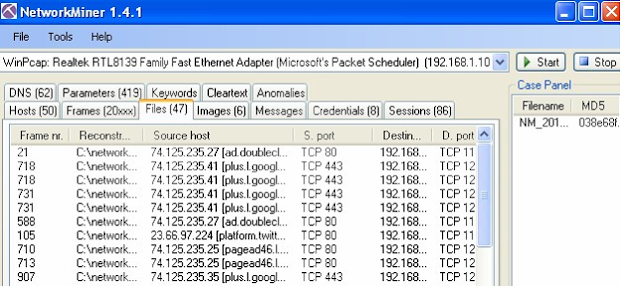
Saat sniffing dengan Network
miner, pengintip dapat melihat data di jaringan, seperti misal gambar.
DNS Server yang digunakan targetpun dapat diketahui
Kita juga dapat mengetahui saat
terjadi sniffing, kita mengetahui source host, source port dan sebagainya.



0 komentar:
Posting Komentar